Login Protection
Data security is of the utmost importance to any CRM system. As such, by default a setting known as “Login Protection” is applied to your Workbooks Account.
Login Protection works to add another layer of security to your Workbooks Account by detecting the IP address a user is logging in from, and the cookie that is stored in their web browser.
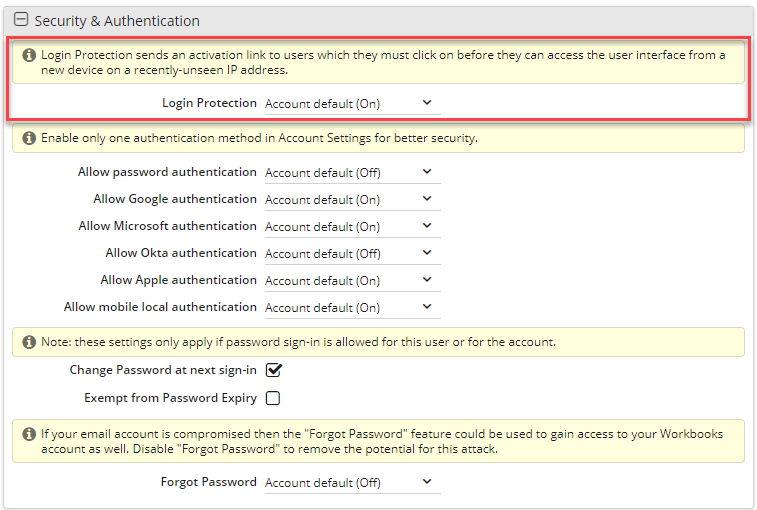
Login Protection can be switched off/on for all of your users from Start > Configuration > Account Settings > Authentication and clicking into the option Additional login security.
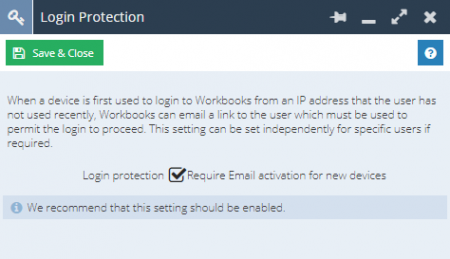
Login Protection can also be controlled on a User by User basis by going to Start > Configuration > Users & Security > Users and opening a User Record.
How does it work?
The Login Protection mechanism looks at two factors:
- Login attempts made from an IP address that has not recently been logged in from by the user (this correlates to a login attempt being made from a new location).
- Login attempts made from a device that has not previously been used to login to that user’s Workbooks Account (this works by looking for a cookie stored on the devices web browser, a new device will not have this cookie on its browser).
If both of the above criteria are met, then the User will be sent an email to verify the login attempt.
Only once the “Confirm Login” button within the email has been clicked will the user be able to login.
Due to the fact that part of Login Protection works by detecting the cookie stored on the web browser of the user’s device, users attempting to access Workbooks using private browser setting such as “incognito” (which stops the cookie mechanism working) will be prompted to confirm their login via email every time they log in from a new IP address.
Note: Login Protection is not to be confused with “Two-factor authentication”. They both work to achieve the same goal of making your account more secure, but have separate mechanisms of doing so. For more information on Two-factor authentication, please see our Knowledge Base page.